
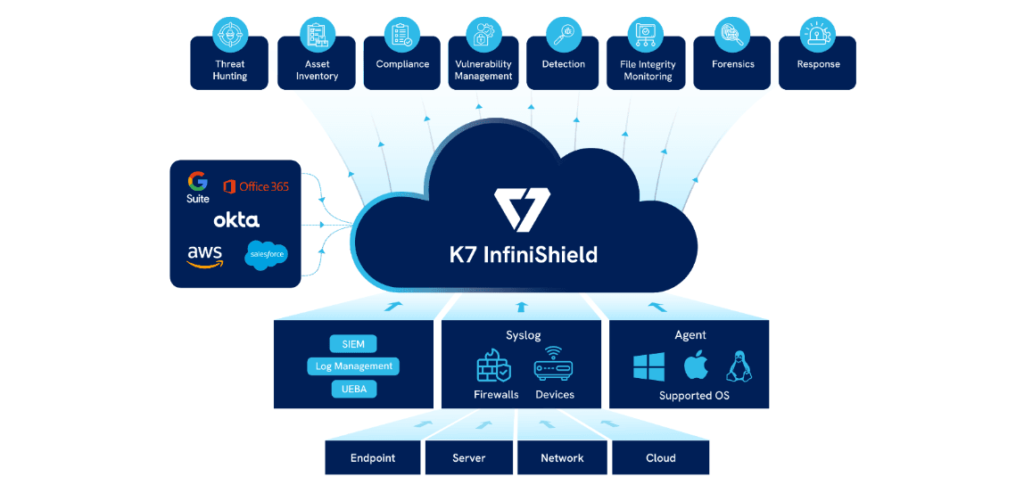
The fragmentation of enterprise cybersecurity increases the cost and complexity of building digital defences and impairs effectiveness as cyberattacks can target the gaps in security infrastructure. K7 InfiniShield provides a single, unified cybersecurity platform that integrates proprietary and 3rd party solutions, manages all digital touchpoints, and delivers quick, actionable insight that enables enterprises to anticipate attacks, automate response, and remediate threats with confidence.
Alerts – Immediate notifications for critical problems.
Graph Explorer – Customizable visualizations allow you to quickly understand the state of cybersecurity and attack trends.
Analytics – Simplified analysis with easily customizable queries for quick retrieval of relevant information.
Asset Inventory – Listing of software packages, editors, users, managed devices, and manufacturers to identify unauthorized use
Continuous monitoring – Real-time monitoring for rapid identification of threats and evaluation and improvement of the security posture
Behavioral analysis – User and entity behavioral analysis (UEBA) allows anomalous behavior to be identified in order to detect and prevent internal threats.
Infrastructure – CPU utilization, memory utilization, and disk space monitoring to understand and investigate performance bottlenecks
Network – Mapping communication between firewalls, switches and other network entities to identify anomalous behavior and unauthorized devices
Application logs – Analysis of application logs to obtain usage metrics and identify errors
Distributed tracking – Simplified visualization of activity paths in digital assets allows identification of potential gaps in defenses and performance restrictions
Cloud – Centralized management of cloud services with monitoring of access logs
User activity – Single-screen display of all activity associated with an account to understand usage patterns
Cloud file storage – Data lake with extensive storage of information on cybersecurity events and granular access controls
Dashboards – Single dashboard view and search across all cybersecurity assets
Managed XDR – Integration of all digital touchpoints for comprehensive cybersecurity
Cloud SIEM – Fully managed SIEM with integration of proprietary EDR and third-party data from any source
Incident Response – Automated threat containment and mitigation
Threat Discovery -Threat detection based on MITRE ATT&CK-based, real-time and AI-enhanced threat detection
Log Management – Comprehensive log management with real-time and archived log analysis
Reports – Customized reports with scheduling support
Integration – The Marketplace for sensors allows integration with any event data source
Playbooks – Orchestrate responses with customizable playbooks that automate cybersecurity processes
Integrated ticketing – Easy SLA management with direct visualization of ticket status from affected assets
SOAR – Comprehensive Security Orchestration, Automation and Response (SOAR) capabilities with support for agentic AI Security Automation and Response (SOAR) with support for agentic AI
Infrastructure Management – Centralized management of end points integrated throughout the company
Remote Access – Authorized remote access to the shell from a browser
Live View – Quick query and analysis of resources with visualizations that allow an intuitive understanding of the results
File integrity monitoring – Protect sensitive information by monitoring the creation, deletion, movement and modification of files
Compliance monitoring – Compliance dashboard and built-in templates for the main standards and regulations